The installers for three different software products developed by the Indian company Conceptworld have been trojanized to deliver information-stealing malware.
The installer works with Notezilla, RecentX, and Copywhiz, according to cybersecurity firm Rapid7, which discovered the supply chain breach on June 18, 2024. The issue was fixed by Conceptworld as of June 24, within 12 hours of responsible disclosure.
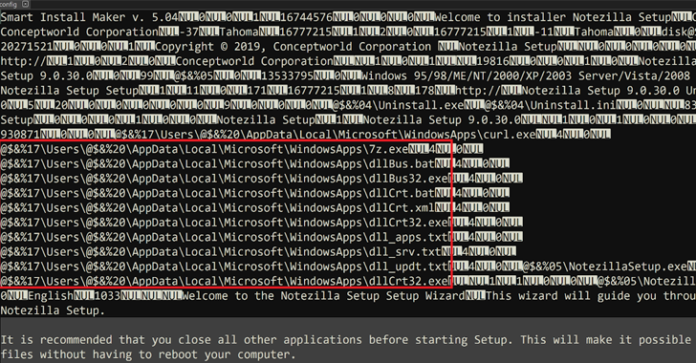
“The installer was trojanized and ran information-stealing malware capable of downloading and executing additional payloads,” the company said, adding that the file size of the malicious version was larger than the legitimate one.
Specifically, the malware is capable of stealing browser credentials and cryptocurrency wallet information, recording clipboard contents and keystrokes, downloading and executing additional payloads on the infected Windows host, and also setting up persistence using a scheduled task to run the main payload every three hours.

At this time, it is not clear how the official domain “conceptworld(.)com” was compromised to distribute the fake installer, but once installed, it prompts the user to continue the installation process associated with the real software, and is also designed to drop and run the binary “dllCrt32.exe” which runs the batch script “dllCrt.bat”.
In addition to establishing persistence on the machine, it is configured to execute another file (“dllBus32.exe”), which establishes a connection with a command and control (C2) server and contains the functionality to steal sensitive data, as well as retrieve and execute more payloads.
This includes harvesting credentials and other information from Google Chrome, Mozilla Firefox, and several cryptocurrency wallets (Atomic, Coinomi, Electrum, Exodus, Guarda, etc.) It is also capable of harvesting files matching a specific set of extensions (.txt, .doc, .png, .jpg), logging keystrokes, and capturing clipboard contents.
“The malicious installer identified in this case was unsigned and the file size did not match a copy of the legitimate installer,” Rapid7 said.
Users who downloaded Notezilla, RecentX, or Copywhiz installers in June 2024 are advised to inspect their systems for indicators of compromise and take appropriate measures, such as reimaging affected systems, to reverse any unauthorized changes.