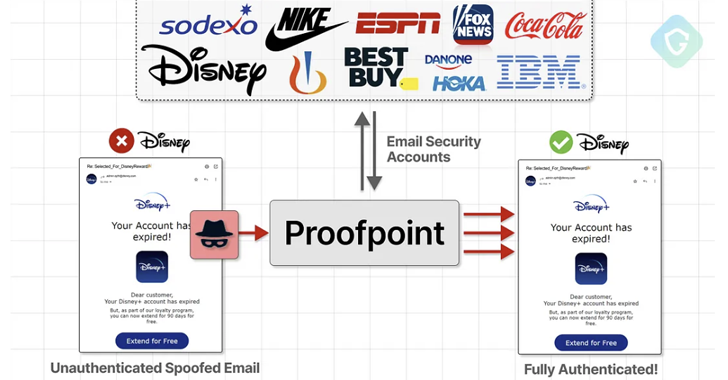
An unknown threat actor has been found to be exploiting an email routing misconfiguration in email security vendor Proofpoint’s defenses, linked to a massive fraud campaign sending millions of messages impersonating a variety of well-known companies, including Best Buy, IBM, Nike, and Walt Disney.
“These emails were sent from official Proofpoint mail relays with authenticated SPF and DKIM signatures, bypassing key security protections – all with the aim of deceiving recipients and stealing their funds and credit card details,” Guardio Labs researcher Nati Tal said in a detailed report shared with The Hacker News.
Cybersecurity companies have been swayed by the campaign. Echo spoofingThe activity is believed to have begun in January 2024, with threat actors exploiting the loophole to send an average of 3 million emails per day, peaking at 14 million in early June when Proofpoint began taking action.
“The most unique and powerful part of this domain is the way it is spoofed, so there is little chance of realizing that this is not a genuine email coming from these companies,” Tull told the magazine.
“This EchoSpoofing concept is really powerful, and it’s a bit odd that it’s being used in a larger scale phishing campaign like this, as opposed to a smaller scale spear-phishing campaign, where attackers can quickly obtain the identities of real corporate team members to send emails to other colleagues, and ultimately, through advanced social engineering, gain access to internal data and credentials, potentially compromising the entire company.
In this technique, threat actors send messages from an SMTP server on a Virtual Private Server (VPS), notably adhering to authentication and security measures such as SPF and DKIM, which stand for Sender Policy Framework and DomainKeys Identified Mail, respectively, and refer to authentication methods designed to prevent attackers from spoofing legitimate domains.

It all comes down to the fact that these messages are routed from various Microsoft 365 tenants controlled by adversaries, then relayed through the email infrastructure of Proofpoint’s enterprise customers, before reaching users of free email providers like Yahoo!, Gmail, and GMX.
This was the result of what Guardio described as a “highly permissive misconfiguration flaw” on a Proofpoint server (“pphosted.com”), which essentially allowed spammers to exploit the email infrastructure to send messages.
“The root cause is that a modifiable email routing configuration feature on Proofpoint servers allows relaying of an organization’s outgoing messages from any Microsoft 365 tenant, but does not specify which M365 tenants are allowed,” Proofpoint said in a coordinated disclosure report shared with Hacker News.
“The email infrastructure that provides this email routing configuration functionality can be exploited by spammers.”

In other words, attackers could weaponize this flaw to set up fraudulent Microsoft 365 tenants and send forged email messages to Proofpoint’s relay servers, from which they would “echo back” as genuine digital messages, spoofing the customer’s domain.
This is accomplished by configuring an outbound Exchange Server mail connector directly to a vulnerable pphosted.com endpoint associated with the customer, and then using a cracked version of legitimate mail delivery software called PowerMTA to send the messages.

“The spammers rotated through virtual private servers (VPS) rented from multiple providers, using various IP addresses to rapidly spam thousands of messages at a time through SMTP servers, which sent them to Microsoft 365 for relay to customer servers hosted by Proofpoint,” Proofpoint said.
“Microsoft 365 accepted these spoofed messages and sent them to these customers’ email infrastructure for relay. If a customer domain was spoofed while transiting through the matching customer’s email infrastructure, DKIM signatures were also applied as the messages passed through the Proofpoint infrastructure, increasing the deliverability of the spam messages.”
EchoSpoofing is suspected to have been deliberately chosen by the operators as a means to generate illicit revenue while simultaneously avoiding the risk of long-term exposure, as directly targeting companies with this technique would have significantly increased the chances of detection, effectively jeopardizing the entire scheme.

That said, it is not clear at this time who is behind this attack campaign, and Proofpoint said the activity does not overlap with any known threat actors or groups.
“In March, Proofpoint researchers identified a spam campaign being relayed through the email infrastructure of a small number of Proofpoint customers by sending spam from their Microsoft 365 tenants,” the company said in a statement. “All analysis indicates that this activity was carried out by a single spam actor, but we do not believe the activity is attributable to any known organization.”
“Since discovering this spam campaign, we have worked diligently to provide corrective instructions, including implementing a streamlined administrative interface that allows customers to specify which M365 tenants they would like to allow relaying from, and denying all other M365 tenants by default.”
Proofpoint stressed that none of its customers had their data compromised or lost as a result of these campaigns, and further stated that it had contacted some customers directly to ask them to change their settings in order to stop the effectiveness of the outbound relay spam operations.
“Once we began blocking the spammers’ activity, they accelerated their testing and quickly moved to other customers,” the company noted. “We have established an ongoing process to identify affected customers on a daily basis and reprioritize outreach to correct their configurations.”
To cut down on spam, the company is calling on VPS providers to restrict users’ ability to send bulk messages from SMTP servers hosted on their infrastructure, and for email service providers to restrict the ability of free trials and newly created, unverified tenants to send bulk outbound email messages and prevent them from sending messages that spoof domains whose ownership has not been verified.
“The main lesson here for CISOs is to be very careful about your organization’s cloud posture, especially your use of third-party services that are the backbone of your company’s network and how it communicates,” Tal says. “Especially in the email space, always maintain a feedback loop and your own control, even if you fully trust your email provider.”
“And for other companies that provide these kinds of backbone services, they need to, as Proofpoint did, first and foremost, be vigilant and proactive about all kinds of threats — not just those that directly impact their customers, but those that impact the general public as well.”
“This is crucial to the safety of all of us, and the companies that build and operate the backbone of the internet bear the greatest responsibility for it, even if they are privately held. As someone said, in a completely different context but very relevant here, ‘with great power comes great responsibility.'”