Spanish-speaking cybercrime groups GXC Team They have been found bundling phishing kits with malicious Android applications, taking malware-as-a-service (MaaS) offerings to a new level.
Singaporean cybersecurity firm Group IB, which has been tracking e-crime perpetrators since January 2023, describes the crimeware solution as an “advanced AI-powered phishing-as-a-service platform” that it says can target users at more than 36 banks and government agencies in Spain and 30 institutions worldwide.
The phishing kits range in price from $150 to $900 per month, while bundles that include the phishing kit and Android malware are available on a subscription basis for around $500 per month.
The attacks targeted users of financial institutions in Spain, as well as tax and government services, e-commerce, banking and cryptocurrency exchanges in the United States, the United Kingdom, Slovakia and Brazil. So far, 288 phishing domains related to this campaign have been identified.
Services offered also include selling stolen banking credentials and custom coding contracting schemes to other cybercrime groups targeting banking, finance, and cryptocurrency businesses.
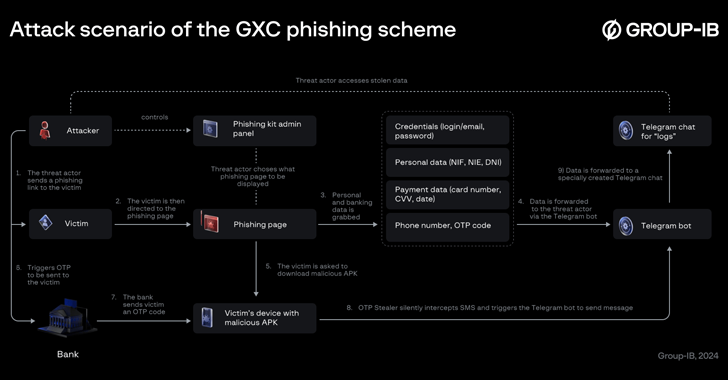
“Unlike typical phishing developers, the GXC team combined a phishing kit with SMS OTP stealing malware, taking a slightly new turn on the typical phishing attack scenario,” security researchers Anton Ushakov and Martin van den Berg said in a report on Thursday.
It’s worth noting here that threat actors are not directly leveraging fake pages to harvest credentials, but instead encouraging victims to download Android-based banking apps to prevent phishing attacks. These pages are then distributed via smishing and other methods.

Once installed, the app requests permission to set itself as the default SMS app, allowing it to intercept one-time passwords and other messages and exfiltrate them to a Telegram bot under its control.
“In the final stage, the app opens the real bank’s website in a WebView, allowing the user to interact with it as normal,” the researchers said. “Then, whenever the attacker triggers an OTP prompt, the Android malware covertly receives an SMS message containing the OTP code and forwards it to a Telegram chat controlled by the threat actor.”
Among other services the threat actors are promoting in their dedicated Telegram channel is an AI-powered voice calling tool that allows customers to place voice calls to potential targets based on a series of prompts provided directly from the phishing kit.
These calls typically pretend to be from your bank and ask you to provide two-factor authentication (2FA) codes, install malicious apps, or perform other arbitrary actions.
“By employing this simple yet effective mechanism, the fraud scenario becomes even more convincing to victims, demonstrating how quickly and easily criminals are adopting and implementing AI tools into their fraud plans, transforming traditional fraud scenarios into new, more sophisticated tactics,” the researchers noted.
In a recent report, Google-owned Mandiant revealed that AI-powered voice cloners have the ability to mimic human speech with “remarkable accuracy,” enabling more realistic-sounding phishing (or vishing) schemes that can facilitate initial access, privilege escalation, and lateral movement.
“Threat actors can impersonate executives, colleagues or even IT support personnel to trick victims into divulging sensitive information, granting remote access to systems or transferring funds,” the threat intelligence firm said.

“The inherent sense of trust that comes with a familiar voice can be exploited to persuade victims to take actions they would not normally take, such as clicking malicious links, downloading malware or leaking sensitive data.”
Phishing kits also feature man-in-the-middle (AiTM) capabilities and are becoming increasingly popular as they lower the technical barrier to entry for conducting large-scale phishing campaigns.
In a report published last month, security researcher mr.d0x said that bad actors could exploit Progressive Web Apps (PWAs) to design convincing login pages for phishing purposes by manipulating user interface elements to display fake URL bars.
Additionally, such AiTM phishing kits can also be used to break into passkey-protected accounts on various online platforms through what is known as an authentication method editing attack, which takes advantage of the fact that even if a passkey is set, these services offer less secure authentication methods as a fallback mechanism.
“By modifying the HTML, CSS, images and JavaScript within the login page, AitM can manipulate the view that the user sees when it is proxied to the end user, allowing it to control the authentication flow and remove all references to passkey authentication,” said cybersecurity firm eSentire.
The revelation comes amid a recent surge in phishing campaigns that use security tools such as Secure Mail Gateways (SEGs) to embed URLs that have already been encoded in order to hide phishing links and evade scanning, according to Barracuda Networks and Cofense.
Social engineering attacks have also been observed using unusual tactics, such as enticing users to visit seemingly legitimate websites and then asking them to manually copy and paste obfuscated code into a PowerShell terminal and execute it, ostensibly to fix issues with viewing the content in their web browser.
Details of how the malware is delivered have already been documented by ReliaQuest and Proofpoint, and McAfee Labs is tracking this campaign under the name ClickFix.
“By embedding Base64-encoded script within a seemingly legitimate error prompt, attackers can trick users into performing a series of actions that result in malicious PowerShell commands being executed,” said researchers Yashvi Shah and Vignesh Dhatchanamoorthy.
“These commands typically download and execute a payload, such as an HTA file, from a remote server, which then deploys malware such as DarkGate or Lumma Stealer.”